In light of the recent news that Google has made the .zip top-level domain (TLD) available for sale, it has become even more crucial to discuss the potential security implications associated with this development. In today’s interconnected world, where cyber threats continue to evolve, phishing remains a significant concern. Phishing attacks exploit human vulnerabilities to deceive and trick individuals into divulging sensitive information or downloading malicious content. This post aims to address the importance of phishing awareness and equip you with practical strategies to navigate this evolving landscape. By understanding the tactics employed by phishers and staying informed about the risks associated with the newly introduced .zip TLD, we can strengthen our defenses and protect ourselves and our organizations from falling victim to these sophisticated attacks. Let’s delve into the fascinating world of phishing awareness and cybersecurity to safeguard our digital identities in this rapidly evolving digital landscape.
.zip will potentially introduce some security implications. Here are a few considerations:
- Phishing Attacks: Malicious actors could exploit the .zip TLD to create convincing phishing campaigns. They might send emails or direct users to websites with URLs ending in .zip, tricking them into believing they are downloading harmless files when, in fact, they could be downloading malicious payloads.
- Malware Distribution: Hackers might abuse the .zip TLD to distribute malware. By hosting malicious files with a .zip extension, they could entice users to download and execute these files, unknowingly infecting their systems with malware.
- File Extension Spoofing: The availability of the .zip TLD might allow attackers to impersonate legitimate files by using a .zip extension. Users might assume they are downloading harmless compressed files but inadvertently execute malicious code instead.
- Bypassing Security Filters: Some security systems and email gateways may have specific filters and rules in place to block or scrutinize certain file types, such as .exe or .js files. If .zip files were allowed as a TLD, attackers could potentially bypass these filters by disguising malicious files within .zip archives.
- File Format Confusion: The use of .zip as a TLD might create confusion among users, as they would need to be cautious when encountering files with the .zip extension. Users might mistakenly assume that all .zip files are safe and could inadvertently execute malicious content.
- User Education Challenges: The introduction of the .zip TLD would require additional education efforts to raise awareness among users about the potential risks associated with downloading and executing files from this TLD. Users would need to be educated about verifying the legitimacy of sources and ensuring the safety of downloaded files, regardless of the file extension.
The Dangers of the Fake Microsoft Email Demonstration
The demonstration in question preys on users’ trust in Microsoft and leverages the familiarity of zip archive files to deceive victims. By mimicking the appearance of a legitimate email from Microsoft, complete with branding and formatting, the attackers aim to trick users into thinking the email and its contents are genuine. The dangers associated with this demonstration are as follows:
- Malware Distribution: The malicious actors behind this demonstration may utilize the .zip domain to distribute malware disguised as a harmless zip archive. Upon downloading and opening the file, unsuspecting users may inadvertently execute malicious code, leading to malware infections and potential compromise of personal or organizational systems.
- Credential Theft: In some instances, the deceptive website launched from the .zip domain may prompt users to enter their login credentials or other sensitive information. These fake login pages are designed to capture the entered data and provide it to the attackers, leading to potential identity theft or unauthorized access to personal or organizational accounts.
- User Interface Deception: The fake user interface within the .zip domain expertly mimics legitimate zip decompression tools. This deceptive tactic aims to fool users into believing they have interacted with a harmless zip archive, reducing their suspicions about the actual nature of the website and its content.
Protecting Against Deceptive Phishing Techniques: To mitigate the risks associated with phishing attacks like the fake Microsoft email demonstration, it is crucial to adopt a multi-layered approach to security. Here are some essential steps to protect against such deceptive techniques:
- Strengthen Email Security: Implement robust email filtering and anti-phishing measures to detect and block suspicious emails before they reach users’ inboxes. Educate users about the warning signs of phishing emails and encourage them to report any suspicious messages.
- User Awareness and Training: Conduct regular security awareness training programs to educate users about the latest phishing techniques, including deceptive email templates and malicious domains. Teach them how to recognize and handle suspicious emails, avoid clicking on unknown links or downloading attachments from untrusted sources.
- Verify Email Sender and Content: Pay close attention to the sender’s email address and check for any inconsistencies or signs of phishing attempts. Be cautious when clicking on email links, especially those requesting downloads or providing login prompts. Verify the legitimacy of emails by contacting the organization directly using trusted contact information.
- Implement Multi-Factor Authentication (MFA): Enable MFA wherever possible, especially for critical accounts and services. MFA adds an extra layer of security by requiring additional verification steps beyond passwords, making it more difficult for attackers to gain unauthorized access.
- Keep Software Updated: Regularly update your operating system, applications, and security software to patch vulnerabilities that attackers may exploit to deliver malware or launch phishing attacks.
- Use Reliable Security Software: Install reputable antivirus and anti-malware software on all devices to detect and block malicious content, including phishing attempts.
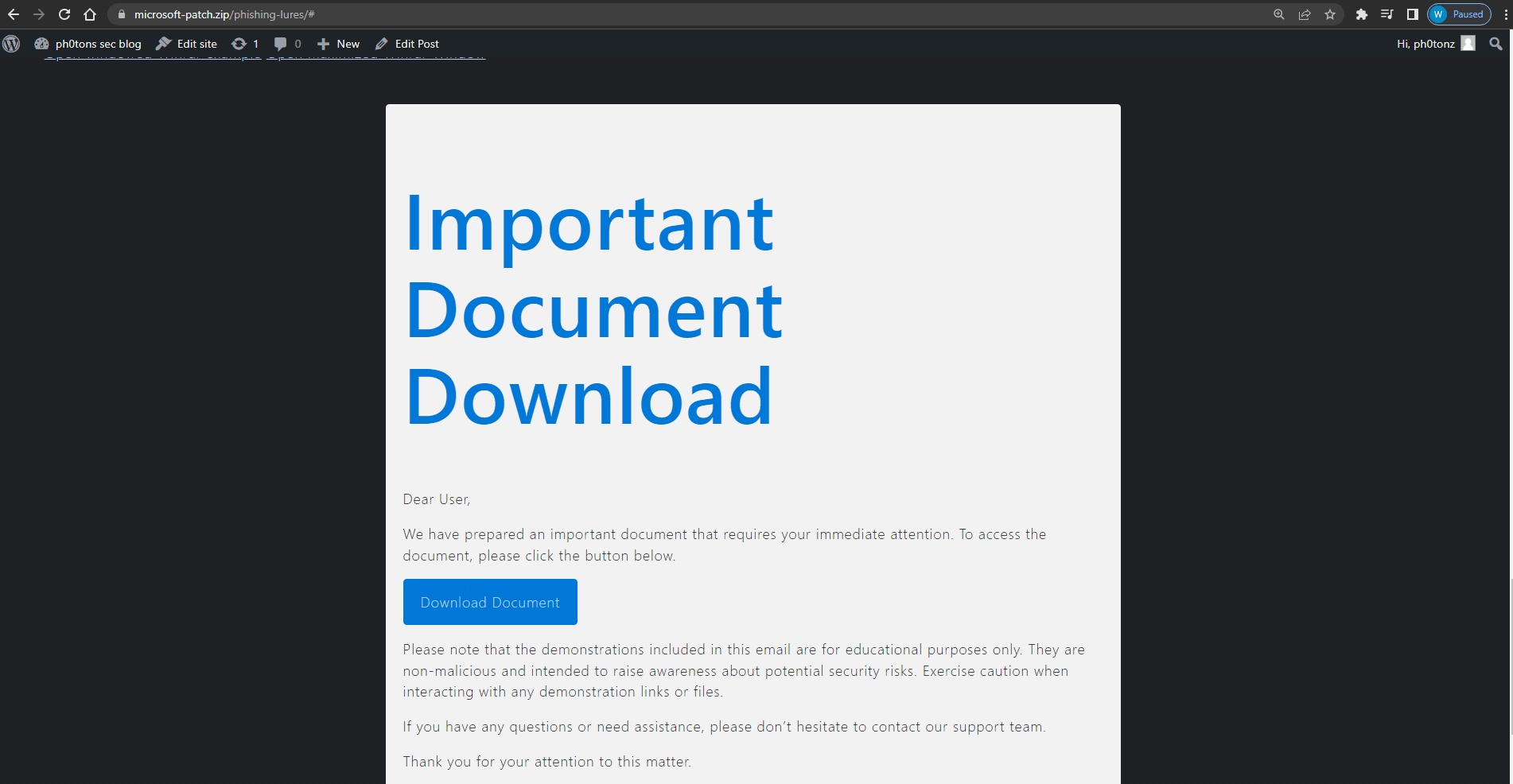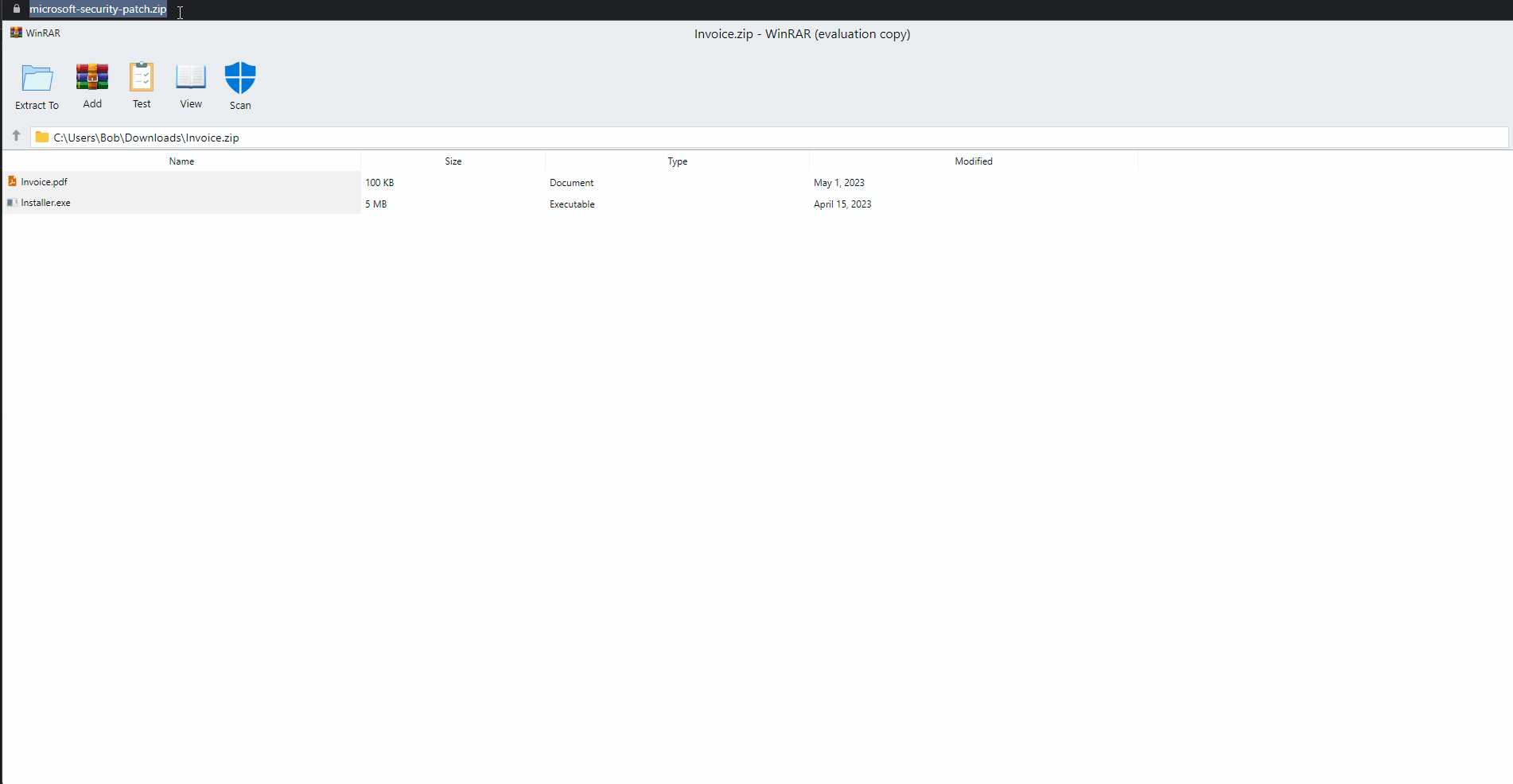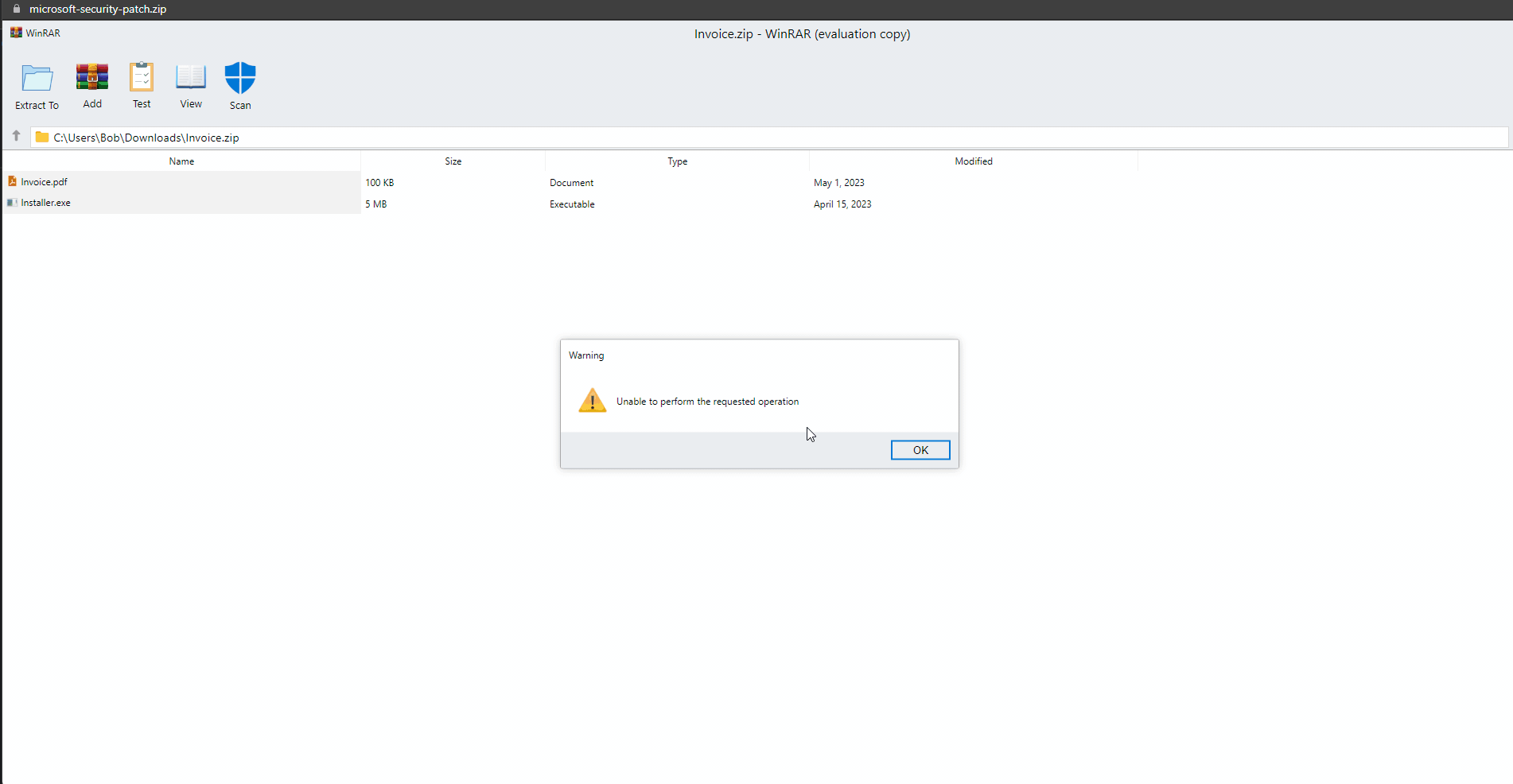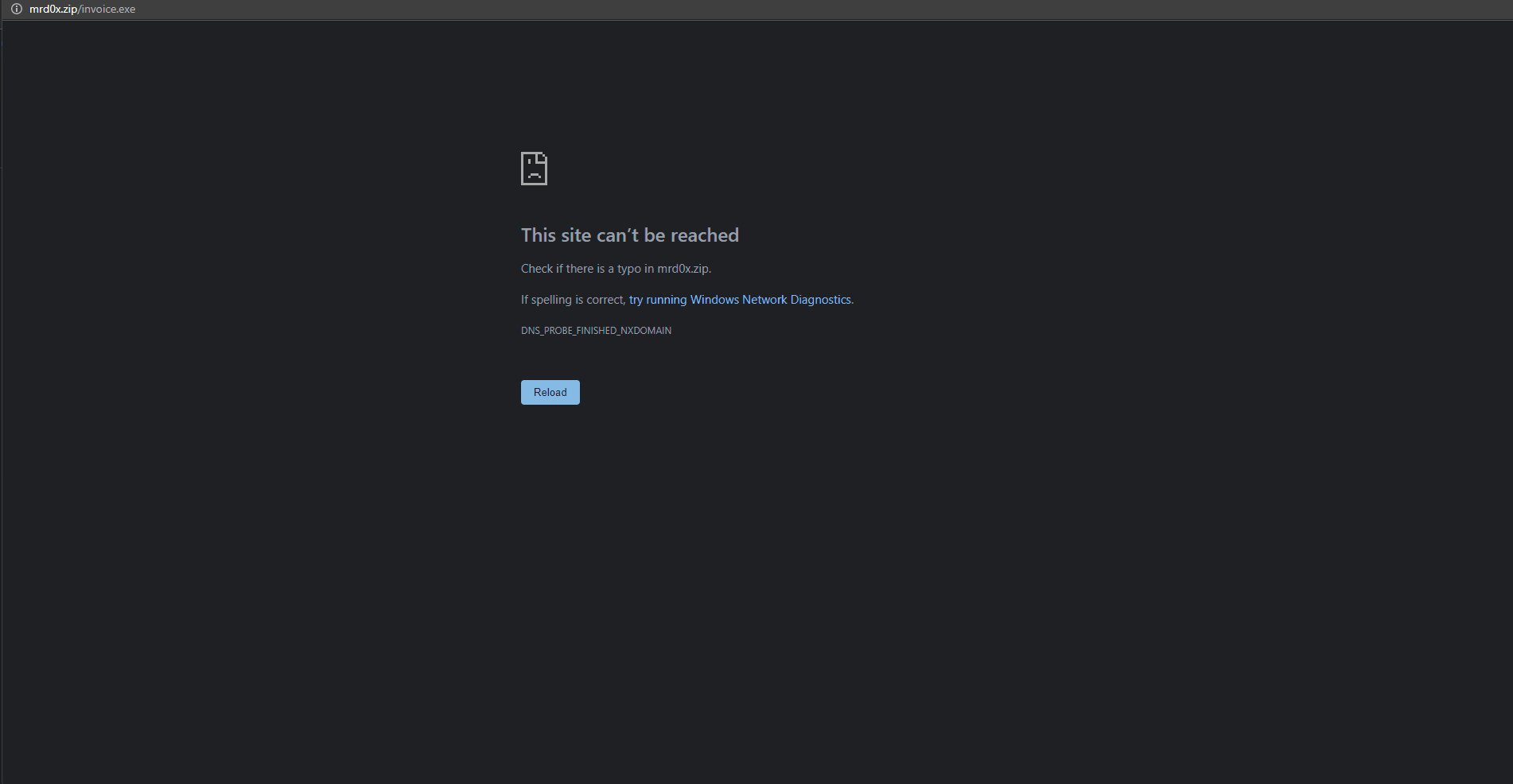
.Zip confusion examples
This example will launch a new browser window and display a fake WinRar interface.
The code used in this demonstration was produced by mrd0x which he kindly released. https://github.com/mrd0x/file-archiver-in-the-browser
Important Document Download
Dear User,
We have prepared an important document that requires your immediate attention. To access the document, please click the button below.
Please note that the demonstrations included in this email are for educational purposes only. They are non-malicious and intended to raise awareness about potential security risks. Exercise caution when interacting with any demonstration links or files.
If you have any questions or need assistance, please don’t hesitate to contact our support team.
Thank you for your attention to this matter.
Best regards,
The MicrosoCKS Team
For those that don’t dare click…

Leave a Reply